The Marketer’s Guide to Secure Document Sharing and External Collaboration
We’ve all been guilty of this at some point. Sharing a sensitive Google doc, spreadsheet, or design file as a public link instead of granting access to specific people. It feels convenient at the moment, but imagine the implications if that one link landed in the wrong hands. It could be by accident or a targeted attack on the company.
That’s why we created this post. Follow along as we explore some of the biggest security and privacy risks of online collaboration and document sharing. This guide will also walk you through the best practices and tools to ensure no private or confidential material can be accessed by unauthorized people.
We’ll be focusing on the marketing department because it exists at the intersection of customer data and business intellectual property, making it a high-value target.

Why secure collaboration matters in today’s campaigns
Here are 4 reasons why secure collaboration should be top of mind for people in marketing.
1. Protection against IP theft and corporate espionage
Imagine your brand’s unreleased campaign materials, such as a rebranding direction, a Super Bowl-level ad, or a creative master file, being exposed ahead of launch.
You lose your competitive advantage because your rivals know your next move. Consequently, you may have to pivot or even scrap the entire campaign, leading to unbudgeted costs, wasted creative efforts, and delays.
Other times, the espionage could go undetected with strategy decks, client lists, and product concepts quietly making their way into the wrong hands.
This is because, with these types of attacks, the threat is usually a trusted insider using legitimate access to steal high-value business intelligence. Implementing employee monitoring tools helps organizations detect unusual behavior, such as unauthorized downloads or late-night file transfers, before they escalate into full-blown data breaches.
Case in point. In March 2025, HR software firm Rippling made headlines after uncovering an elaborate espionage scheme between an employee and a rival firm, Deel. The employee admitted to accepting a $5000 monthly payment in exchange for confidential information, including customer data, pricing information, competitive intelligence, and Rippling employee data for targeted recruiting.
2. Guarding the business against costly cyberattacks
Beyond espionage, marketing and creative teams are also prime targets for cybercriminals seeking financial gain. Once inside your system, attackers can lock you out of ongoing projects or steal sensitive data, demanding a ransom to restore access.
In 2024, Disney was a victim of a major attack in which the hacker gained access to thousands of unsecured Slack channels, stealing 1.1TB of data. The exposed information included unreleased project details, financial records, proprietary source code, and employee personal data.
Hackers can also use the marketing department as the gateway to other, more critical business levels like finance and IT. For instance, they could exploit a poorly secured shared file or collaboration link to deliver malware or insert a phishing link targeting senior executives and other high-value targets. Cybercriminals frequently use email to spoof your brand’s domain, making phishing links or malware attachments look completely legitimate to an unsuspecting colleague or client. That’s why a simple check like an EasyDMARC dmarc checker can quickly confirm that you have the right protections in place to stop criminals from sending emails using your company’s name.
The handling of sensitive customer data like names, email, and addresses means the marketing department falls under data privacy regulations, such as:
- General Data Protection Regulation (GDPR)
- California Consumer Privacy Act (CCPA)
- Digital Services Act (DSA)
- Health Insurance Portability and Accountability Act (HIPAA)
Therefore, when a breach occurs it’s not just a technical mishap. It’s a legal liability that can result in multi-million-dollar fines.
In 2022, Sephora, a cosmetics company, was fined $1.2 million for failing to disclose that it sold customer data to third parties and didn’t honor “Do Not Sell My Personal Information” requests under the CCPA.
3. Protecting your brand’s reputation and customer trust
When cases of corporate espionage, major data breaches like the Disney hack, or compliance failures reach the public, the fallout is immediate and often irreversible. Clients and partners start questioning your ability to safeguard their information and projects.
This directly impacts your bottom line, leading to canceled contracts, lost partnerships, and difficulty acquiring new business. You become a cautionary tale. A case study.
All because you forgot to revoke permissions after a freelancer ended their contract.
Common challenges in secure collaboration when working with external partners
These are the biggest challenges you’ll encounter when trying to secure collaboration.
1. Too many tools
Marketing teams love their tools. Project managers in Asana, clients commenting in Google Drive, and presentations shared through email or Slack and other workplace communication tools. But when collaboration happens across so many platforms, gaps appear. And unfortunately, not all tools prioritize security, creating weak links an attacker can exploit.
2. Use of unsecured channels for sensitive information
It’s common for team members to bypass secure file-sharing systems in favor of unsecured but usually more convenient methods like personal email and direct messages. This leaves sensitive data like contracts, campaign budgets, or personal data (PII) stored on servers you don’t control and with no auditable trail for your security team to follow.
3. Inconsistent access management
At first, it’s usually very easy to keep track of who has access to what. However, as more assets are shared and new collaborators join and leave, the permissions can spiral out of control. Former freelancers, vendors, or even ex-employees may still have entry points into live projects, which could lead to accidental or intentional leaks.
4. The human factor
Even the most secure platform can’t prevent human error. A freelancer reusing weak passwords. An employee falling for a phishing link. A rushed campaign handoff leading to a mis-shared folder. Disney was hacked because an employee logged in to his business account using a personal device infected with malware. Social engineering remains one of the top causes of breaches because it exploits the one thing no software can fully secure: people.
5. Compliance and regulatory pressures
Approximately 30% of data breaches in 2025 involved a partner, vendor, or external service. When you share sensitive data with a contractor, agency, or vendor that is not compliant with GDPR, CCPA, HIPAA, or industry standards like ISO and SOC 2, you assume their risk. A security failure on their end becomes your breach and your responsibility.
7 best practices for secure collaboration with external partners
Now that you understand the risks and challenges of secure collaboration and document sharing, the next step is to set up the right security controls.
These seven best practices help marketing teams protect creative assets, client data, and brand integrity while maintaining productivity.
1. Use centralized and secure platforms
The first step to secure collaboration is consolidation. When your team spreads its work across too many tools, visibility and control disappear, and every additional platform introduces a new potential vulnerability. By bringing your projects together in a single, secure environment, you simplify access management and reduce the risk of leaks or data exposure.
That said, finding an all-in-one marketing platform for design collaboration, document sharing, communication, and project management is challenging. Most teams still rely on a mix of specialized tools for different tasks. The key is to ensure that each tool you use meets strong security standards and integrates safely with the rest of your workflow.
For instance, Flipsnack allows marketing teams to create, share, and track interactive brochures or campaign material while also incorporating tight access control features.
2. Control access and permissions
Access should always be intentional and follow the principle of least privilege. Only grant collaborators the permissions they need to do their job. If the tool allows, set an expiration date for shared links so that once a project wraps, so does access to your brand’s assets.
Also, ensure that you enforce multi-factor authentication for all accounts. This way, if login credentials are exposed, there’s an extra layer of security. For added protection, use advanced access controls such as geo-blocking to limit logins from unknown or high-risk regions or IP allow-listing to ensure files can only be accessed from a known, authorized corporate IP address.
3. Encrypt and protect shared files
Always assume that a shared file could fall into the wrong hands. Encryption and password protection ensure that only authorized people can read the contents of a file. Just be sure to use premium and proven tools. Free tools often lack tight security controls or can be easily bypassed.
Another great tip is to add watermarks and enable tracking for shared content. A watermark embeds the viewer’s personal identifier (like their name, email, or IP address) directly onto the file. Consequently, if that document is leaked, screenshotted, or photographed, the watermark instantly identifies the source, turning the document into a traceable asset. This helps maintain visibility and accountability throughout the collaboration process.
4. Adopt a Zero Trust Model
Zero Trust is a simple but powerful concept: never trust, always verify. Every user, device, and login attempt should be authenticated before access is granted. The reason for this is simple. Hackers are increasingly using stolen credentials to gain legitimate access to target accounts. And the scary part is, you could be a data breach victim and you have no idea.
It is estimated that over 60% of US residents have had their personal data breached at some point, with 44% of those experiencing multiple breaches. Consider using an identity theft protection tool like the one from Aura to get notified when your information is exposed in a data breach.
5. Regularly audit and monitor access
Maintain detailed access logs to track who viewed, edited, or downloaded assets. Additionally, review permissions regularly and revoke access immediately when projects end or roles change. You can choose to do this manually but it’s usually tiresome and prone to error. Using enterprise search makes this process easier. It automatically indexes files across multiple tools and shows where sensitive assets live, who has access, and whether any external collaborators or ex-freelancers still retain unwanted permissions. Instead of hunting through individual folders or apps, you have full visibility in one place.
Automating the process empowers you to go beyond simple logging to even implement behavioral analytics. This way, you can get alerted when there’s suspicious behaviour, like an employee who’s already clocked out logging in to their account.
6. Educate teams and partners on cybersecurity
Your security posture is only as strong as your least-informed team member. Regularly train employees, contractors, and partners on phishing awareness, secure password practices, and device security. Educate them on the importance of managing their digital footprint to avoid accidentally giving out information that hackers can use for refining their social engineering tactics.
Moreover, establish clear collaboration guidelines so everyone understands how to share and store assets safely. A culture of security awareness is one of the best defenses against human error.
7. Have a disaster recovery plan
Even with the best safeguards, mistakes and attacks can still happen. Prepare accordingly. Back up brand assets and campaign files regularly, and store those backups in secure, encrypted environments. A strong disaster recovery plan ensures business continuity and peace of mind, allowing your marketing operations to recover quickly if the unexpected occurs.
Your customers and partners should also be part of your disaster recovery plan. Put measures in place to ensure prompt disclosure and damage control. For instance, you can offer to provide free credit monitoring if their financial details have been exposed. These steps are critical in rebuilding customer trust and brand reputation.
What are the most secure collaboration tools in 2025?
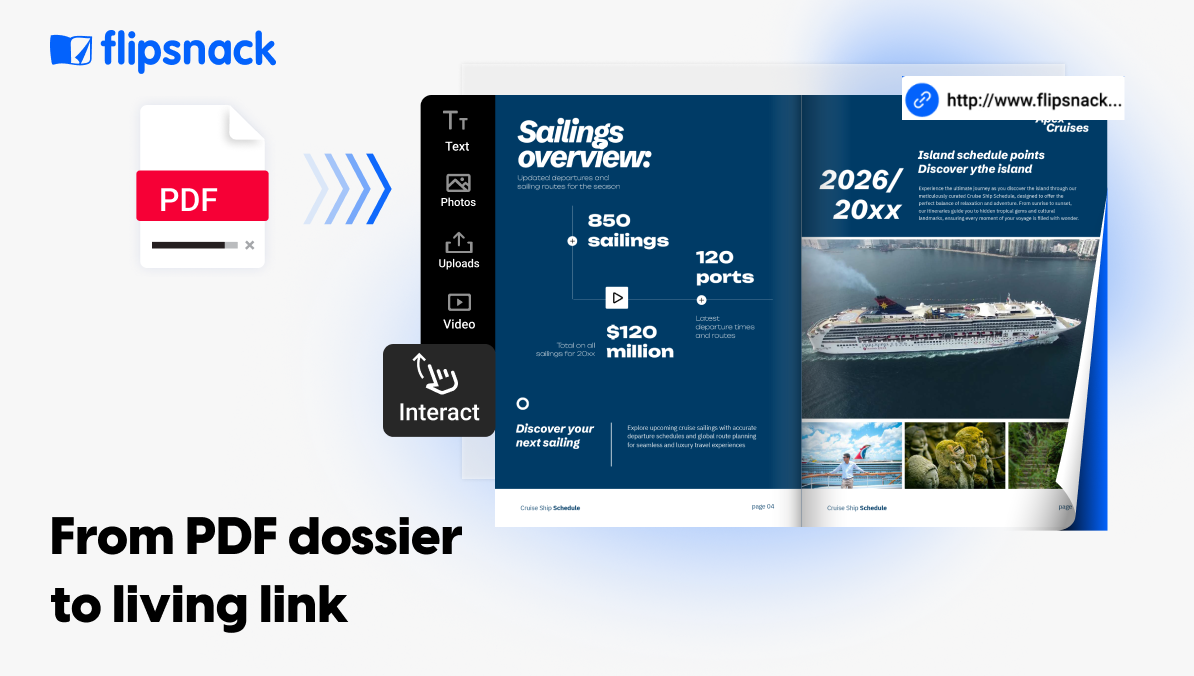
1. Flipsnack: Best for sharing and managing creative assets securely
Flipsnack is a tool that lets marketers turn static PDFs into interactive, page-flip digital publications. It’s perfect for businesses looking to improve static marketing documents with engaging, multimedia-rich content. The flipbook can easily be shared through a direct link, via email, or privately with a selected audience. Flipsnack lets you access insights such as clicks and average time spent reading your PDF flipbook, along with a heatmap and AI-generated insights based on individual flipbook reports.
To keep client materials and internal assets secure, Flipsnack includes an array of secure sharing options:
- Password protection and one-time passcodes to restrict access to only the people you choose
- Private or unlisted Links to share content securely without making it publicly searchable
- Domain restrictions to limit viewing to your agency website or a specific domain
- Role-based access controls to ensure only authorized team members can view, edit, or share files
- SSL encryption and secure hosting to protect data both in transit and at rest
- ISO certified – Keeps your workflows aligned with international privacy standards
Pricing
Flipsnack is available in different plans starting at $16 per month.

2. Google Workspace: Best for real-time document collaboration
If you’re looking to collaborate on documents, spreadsheets, slides, and sharing drafts with internal teams or external parties in real time, Google Workspace is the tool for you. It’s simple to use and widely used. Every change you make to a file is updated automatically eliminating the need to send files back and forth. Collaborators can also highlight a specific part they want to change and leave a comment for others to see.
To ensure secure team collaboration Google Workspace offers:
- Granular sharing permissions – Decide who can view, comment, or edit each file.
- Encryption in transit and at rest
- Admin console oversight – Gives marketing leads full control over access and sharing settings.
Pricing
Google WorkSpace is available starting at $7/user/month.
3. Microsoft Teams: Best for enterprise-level collaboration and file-sharing
Microsoft Teams brings together chat, video meetings, file sharing, and collaboration tools, all within one secure environment. Perfect for large marketing departments and agencies managing multiple client accounts, Teams integrates smoothly with Microsoft 365 apps like Word, Excel, and SharePoint for end-to-end project management.
Google Workspace ensures your files and communication stay private with:
- Advanced data encryption in transit and at rest.
- Information barriers & retention policies – Control who can communicate internally and how long data is stored.
- Secure guest access – Collaborate with clients or freelancers safely within Teams’ controlled environment.
4. Slack: Best for streamlined communication with external partners
Slack simplifies communication for marketing teams that collaborate with clients, freelancers, and external partners daily. Its intuitive channels, threads, and file-sharing tools keep everyone aligned without endless email chains. You can even integrate tools like Google Drive, Asana, or Figma for smoother project flow.
To keep your agency’s conversations and shared files secure, Slack includes:
- Data encryption at rest and in transit.
- Controls over who can join channels or view sensitive conversations.
- Secure external collaboration (Slack Connect) – Enables safe, verified communication with clients and vendors.
5. Asana: Best for secure campaign workflow management
Asana helps marketing teams plan, track, and execute campaigns with total clarity. From managing content calendars to launching multi-channel campaigns, it turns complex workflows into simple visual boards, timelines, and task lists that everyone can follow.
Asana provides strong security and privacy protection through:
- Role-based access controls
- Data encryption at rest and in transit
- Audit logs and admin controls
6. Clean Email: Best for secure and privacy-focused inbox management
If your team’s inboxes are overloaded with newsletters and promotional emails, Clean Email helps you keep everything tidy and private. It’s perfect for marketers and remote teams who want to manage clutter without exposing sensitive data. The tool automatically groups similar emails, unsubscribes you from unwanted senders, and applies filters to keep only relevant messages.
To ensure data security, Clean Email offers:
- Encryption in transit and at rest
- OAuth login – no password sharing required
- Zero data access – your email content stays private
Pricing
Clean Email plans start at $9.99/month.
Key takeaways about secure document sharing
Modern marketing teams are not just sharing simple designs and content calendars; there’s also critical intellectual property, strategic plans, partner contracts, business analytics, client pipeline data, etc. Without proper security controls, hackers or a malicious insider can easily gain unauthorized access to key business assets, which can have devastating consequences. With this guide, you now have actionable steps as well as secure collaboration tools that you can adopt to strike the right balance between security and speed.